Hi,
I need to add an event to the AAD group calendar.
Webcon uses/is synced with local AD.
AD is synchronized with AAD.
On the AAD side, an application with API permissions has been added
Adding AAD groups and adding users to groups via graph API from webcon works fine.
But, for example, if you want to add an event to the group's calendar
POST method https://graph.microsoft.com/v1.0/groups/{group_id}/calendar/events
The api needs to run in the context of the logged in user, not in the context of the application.
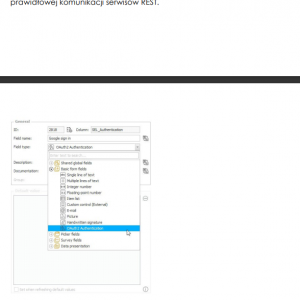
That's why I added authorizations in webcon: screen1
I added a connection to this authorization: screen2
Then in the REST action I added this connection.
On the graph api side, added Group.ReadWrite.All delegated permissions, approved by the admin.
The user who invokes the rest actions is the owner of the AAD group.
When calling the action, I get the error: screen3
Response Code:
exceptions:
There is no valid token for connection: [TEST]_Azure_APi_User (13)
So the user did not receive the token.
So the question is whether such a scenario is possible or whether something else should be configured.
I will be grateful for your help.
User > API authorization
Hi Karol,
F1 doesn't show any help on this topic in Designer Studio, but thankfully it's pretty well documented in changelog when that functionality has been introduced: https://community.webcon.com/download/changelog2/51?q=34ce750 - it's around 6th page :)
From what i see you have to add OAuth2 Authentication field on the form, so the user will be able to login with OAuth.
Hi Karol,
F1 doesn't show any help on this topic in Designer Studio, but thankfully it's pretty well documented in changelog when that functionality has been introduced: https://community.webcon.com/download/changelog2/51?q=34ce750 - it's around 6th page :)
From what i see you have to add OAuth2 Authentication field on the form, so the user will be able to login with OAuth.
thank you Maksymilian,
I just couldn't find any documentation/description for this.
Now it works properly.
thank you Maksymilian,
I just couldn't find any documentation/description for this.
Now it works properly.
I'm glad it works!
It would be good to have it documented in Designer Studio though (i'm running 2021.1.5.367 and F1 doesnt bring any help on authentications, maybe it's in later versions), and not have to look through changelogs to find it.
Could we get some response from Webcon Stuff on this maybe?
I'm glad it works!
It would be good to have it documented in Designer Studio though (i'm running 2021.1.5.367 and F1 doesnt bring any help on authentications, maybe it's in later versions), and not have to look through changelogs to find it.
Could we get some response from Webcon Stuff on this maybe?
Hello,
I have another question, has anyone automated this case, using a method that requires an authenticated user.
I would like to use it in a recurring action, running in the context of a service account.
Regards.
Hello,
I have another question, has anyone automated this case, using a method that requires an authenticated user.
I would like to use it in a recurring action, running in the context of a service account.
Regards.
I'd try configuring it with application permissions instead of delegated permissions then - similar as for mailapprove and mailbox.
Everytime you don't want user to sign in to their own accout - you have to use application permissions.
Basically follow this to create application, user, group:
https://kb.webcon.pl/10159-2/
Then instead of OAuth2 User -> API Authentication create OAuth2 App -> API Authentication.
I'd try configuring it with application permissions instead of delegated permissions then - similar as for mailapprove and mailbox.
Everytime you don't want user to sign in to their own accout - you have to use application permissions.
Basically follow this to create application, user, group:
https://kb.webcon.pl/10159-2/
Then instead of OAuth2 User -> API Authentication create OAuth2 App -> API Authentication.
Thanks for the answer, but operating in the context of delegated permissions is required by the Graph Api for some methods,
That's why I posted this post.
Operation in the context of application permissions is ok and OAuth2 App -> API Authentication is not required.
It is enough to use a properly configured connection with Graph Api authentication.
Thanks for the answer, but operating in the context of delegated permissions is required by the Graph Api for some methods,
That's why I posted this post.
Operation in the context of application permissions is ok and OAuth2 App -> API Authentication is not required.
It is enough to use a properly configured connection with Graph Api authentication.
Ah yes i can see it in graph documentation, sorry i lost that part from main post.
With technical user it'll be hard to achieve. From what i understand end user can't have permissions to acess that calendar?